

I think it eventually got challenged and banned. The response from the SPD party was “We were just getting started, our campaing will be even more harsh.”
It is just a bunch of idiots, what can I say.


I think it eventually got challenged and banned. The response from the SPD party was “We were just getting started, our campaing will be even more harsh.”
It is just a bunch of idiots, what can I say.
On the topic of Mullvad, what made me choose Kullvad over LibreWolf was the VPN being bundled in. If I’m not mistaken, the whole point of ToR browser is that you have exactly the same fingerprint as any other Tor browser user, making it a lot harder to distinguish you from others using your extensions, browser and other minor stuff your browser reports about you, that combined makes for a pretty unique fingerprint, evej of you are using a VPN.
But, if you have a browser that has the same fingerprint for all users, and it has an accompanying VPN, you can partly expect that most of other users of the same VPN will also be using the same browser, making it a lot harder to track you - because while there may be only a few thousands users of Mullvad in the wild, which renders the same fingerprint not much of an advantage (because you would be one of the few users of i.e Proton VPN with Mullvad), if you also use Mullvad VPN, it’s probable that most of other users who share your Mullvad VPN IP are also Mullvad browser users, making it easier to blend in.
Bit that’s mostly my theory, why (along with being able to pay with Monero) I feel like the combo of Mullvad browser and VPN is the best combination as far as minimizing fingerprint is considered. If someone has more knowledge about the issue, I’d love to hear some counter-arguments or tips how to improve my setup.


EVE is one of the most unique games I’ve ever seen and I admire it, and CCP in general, from what I’ve seen in their volunteer programs or from streams, seems like a nice workplace.
Also, Island is cool.


Then the book will definitely be up your alley, it’s exaclty about that, and offers a great tips about how to approach it.


I cheated the MFAs by switching what I could to SMS, Yubikey or just copying the MFA private keynto Bitwarden. Kind of defeats the point of MFA, but makes stuff definitely easier.
Anything that’s important however is on yubikey, however.
Also, good luck! Are you going through the Digital Minimalism book? I should refresh on it, every time I try it, it doesn’t last long, but I always get rid of one more stupid online habit that I don’t pick up when I inevitably return to my pre-reading the book intetnet usage. So, after already going through like 4 attempts in the last 3 or 4 years, my internet usage is slowly but surly changing for the better. But it’s more of a long run, rather than being able to get everything on the first try, in my experience at least.
If you’re not doing it because of the book/haven’t heard of it, I definitely recommend reading Digital Minimalism by Carl Newport.


How to best approach starting secops in a small indie gamedev studio. We don’t even have a sysadmin, and our boss mostly also does most of our infra together with one of the programmers.
We would love to start setting up some basic security setup, ideally FOSS based, and while I work there as a programmer, I do have 5 years of experience working as pentester and doing red teamings, so I kind of have an idea about what we could have. But I never did anything from blue team side, and also worked for large corporations, so most of the tools and solutions I’ve encountered are waaay over the budged of 20 man indie gamedev studio.
How would I even start? Are there any frameworks that would help but arent aimed at large corporations? What of the buzzwords we even need? Do I start with hardening group policies, get rid of local admins, then set up some kind of log management/SIEM, then IDS? And it’s so hard to google for, because every blog post I found is just a disguised ad for a company that does Security as a Service. Why isn’t there some kind of easy 10 step program that would tell you “step 1. Harden configuration. Step 2. Install <one of many security tooling acronyms>.”
I vaguely know that most of the buzzwords that are thrown around have some dependencies, but what? Does IDS needs logs from SIEM, or is it the other way around? I’m obviously not qualified for this, but i dolid get time to research it, and some DIY attempts is definitely better than having no security in place at all. And, I know very well how to actually hack and test our security setup, so I can at least tell if something I’ve done is shit or useless :D


I’d go for scandiavia, if I could choose anywhere. Or Island, working for CCP is my dream job.


When I tried that, it lasted me for almost a year and a half, before I unfortunately got a second job that required MFA and I needed to be more online in general due to juggling two jobs. And it was amazing!
What I eventually did however was to get a dumb phone that can do a wifi hotspot, and still carried my smartphone but without simcard and net access, and powered off. When I really needed to get a taxi or look up a way home when I overslept drunk on public transport and ended up who knows where, I could always just fire up hotspot, power on the smartphone and do stuff I needed. Cause when that happened first time, it was when I first realized how much dependent I am on smartphone and net access.
Thanks for reminding me, I just quit one of the jobs and I can afford to be more offline, so back to the dumb phone I go! Convincing my GF again that she has to text me instead of using discord will be hard, though … Or explaining that I really cant look up the fact she wants, or call a taxi quickly…
I still have a python bot that forwarded discord messages to my own bare html website, so I can chat with her with the basic web browser of the dumb phone.


That’s not even the worst poster they have. They also have this one:
Healtcare shortcomings won’t be solved by imported ‘surgeons’
Stop the EU migration pact

I hate those pieces of shit so much. And this is a real election campaign poster.
I can’t decide whether this sentence is a joke or not. It has the same tone that triggers my PTSD from my CS degree classes and I also do recognize some of the terms, but it also sounds like it’s just throwing random science terms around as if you asked a LLM to talk about math.
I love it.
Also, it’s apparently also real and correct.
VRAM would be 810Gb/403Gb/203Gb for FP16/FP8/INT4 for interferrence, according to their website.
I’m not sure what “FP16/FP8/INT4” means, and where would GTX 4090 fall in those categories, but the VRAM required is respectively 810Gb/403Gb/203Gb. I guess 4090 would fall under the INT4?
I mean, if it’s **just ** a normal screen-sized website, that already makes it a lot easier. Not having to deal with responsiveness bullshit would make webdev a lot better experience. That is assuming “normal screen” means 1920*1080, or whatever is the median screen size.


Heh, guess it’s really only your national tragedy. Keep your secrets, then.


I might be wrong, but from how I understand it it probably wouldn’t help. Kernel drivers have a rigorous QA and cert by Microsoft if you want to get them signed, which is a process that may take a long time - longer than you can afford when pushing updates to AV/EDR to catch emerging threats. What Crowdstrike does to bypass this requirement is that the CS Falcon is just an engine, that loads, interprets and executes code from definition files. The kernel driver code then doesn’t need to change, so no need for new MS cert, and they can just push new definition files. So, they kind of have to deal with unsafe in this case, since you are executing a new code.


It has been a while since I have to deal with problem complexities in college, is there even class of problems that would require something like this, or is there a proven upper limit/can this be simplified? I don’t think I’ve ever seen O(n!^k) class of problems.
Hmm, iirc non-deterministic turing machines should be able to solve most problems, but I’m not sure we ever talked about problems that are not NP. Are there such problems? And how is the problem class even called?
Oh, right, you also have EXP and NEXP. But that’s the highest class on wiki, and I can’t find if it’s proven that it’s enough for all problems. Is there a FACT and NFACT class?


Here is a picture, that may help a little bit. The n is input size, and f(n) is how long does the algorithm runs (i.e how many instructions) it takes to calculate it for input for size n, i.e for finding smallest element in an array, n would be the number of elements in the array. g(n) is then the function you have in O, so if you have O(n^2) algorithm, the g(n) = n^2
Basically, you are looking for how quickly it grows for extreme values of N, while also disregarding constants. The graph representation probably isn’t too useful for figuring the O value, but it can help a little bit with understanding it - you want to find a O function where from one point onward (n0), the f(n) is under the O function all the way into infinity.
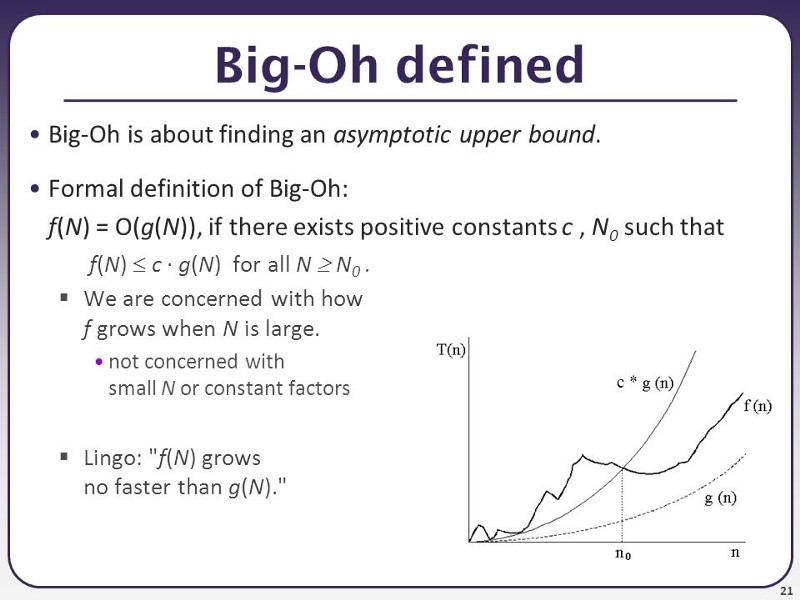


For me, my common result would be something like O(shit).


Exactly this. I only have pretty vague experience with machine learning, since it was one of the other specializations for my Masters than the one I choose, which however means we still shared some basic courses on the topic, and I definitely share his point of view. I’ve been saying basically the same things when talking about AI, albeit not as expressively, but even with basic insight into ML, the whole craze that is happening around it is such bullshit. But, I’m by no means an expert in the field, so I may be wrong, but it’s nice to finally read an article from an “expert” in the field I can agree with. Because so far, the whole “experts talking AI” felt exactly like the COVID situation, with “doctors” talking against vaccines. Their doomsaying opinion simply contradicts even the little knowledge I have in the ML field.
As someone who works in gamedev, I’m sure that some of the people there are passionate about it and it is gutwrenching to see your work fail so hard. I’m sad for every project that launches after years of work and fails to get any attention or sales, and I’m definitely sure there’s someone losing sleep due to that.
I never worked in super-large projects, but I did work for a AAA studio and even there, you got people invested into the project.
From how I’ve seen it, you wouldn’t work in gamedev unless you are passionate about it, because you can get drastically better pay for the same job in other, more business focused, industries. So, if all you cared about is money, you have better options.