Vulnerabilities in Sogou Keyboard encryption expose keypresses to network eavesdropping.
As if other keyboard apps are any different, I don’t think Microsoft bought SwiftKey just for fun?!
Really? Isn’t this kind of thing scandalous enough to tank companies?
It’s in their EULA read their terms of services
In a surprise to absolutely nobody, China spies on their people.
As opposed to which country?
And everyone’s people
TIL this only happens in China

It’s not a bug, it’s a feature.
So when the Chinese do it it’s scary, but when the Americans do it it’s just “established practice”?
Neither of the groups should be allowed to do it.
Whataboutism doesn’t really apply when pointing out a double standard. It’s true that both places shouldn’t do the bad thing, but it’s more about the individual’s reaction to that thing depending on who does it. The average US citizen will criticise the CCP for doing plenty of the same things their government currently does, or has done in the past, that they support.
Furthermore, it’s important to note that when this kind of thing happens, people treat it as China’s government’s fault, but when Tesla cars explode, people don’t consider that the US government’s fault.
I don’t get it? Why are they talking in the article about not using the right type of encryption. The problem isn’t the encryption, but the fact that it is sending your keystrokes to the mothership, right?
“Notice the lack of surprise.”
China being China, no surprise here.
And the Platinum Award for Least Surprising News Headline goes to…
Naomi Wu has literally been talking about pwnd Chinese IMEs for years in her sidechannel critiques of Signal.
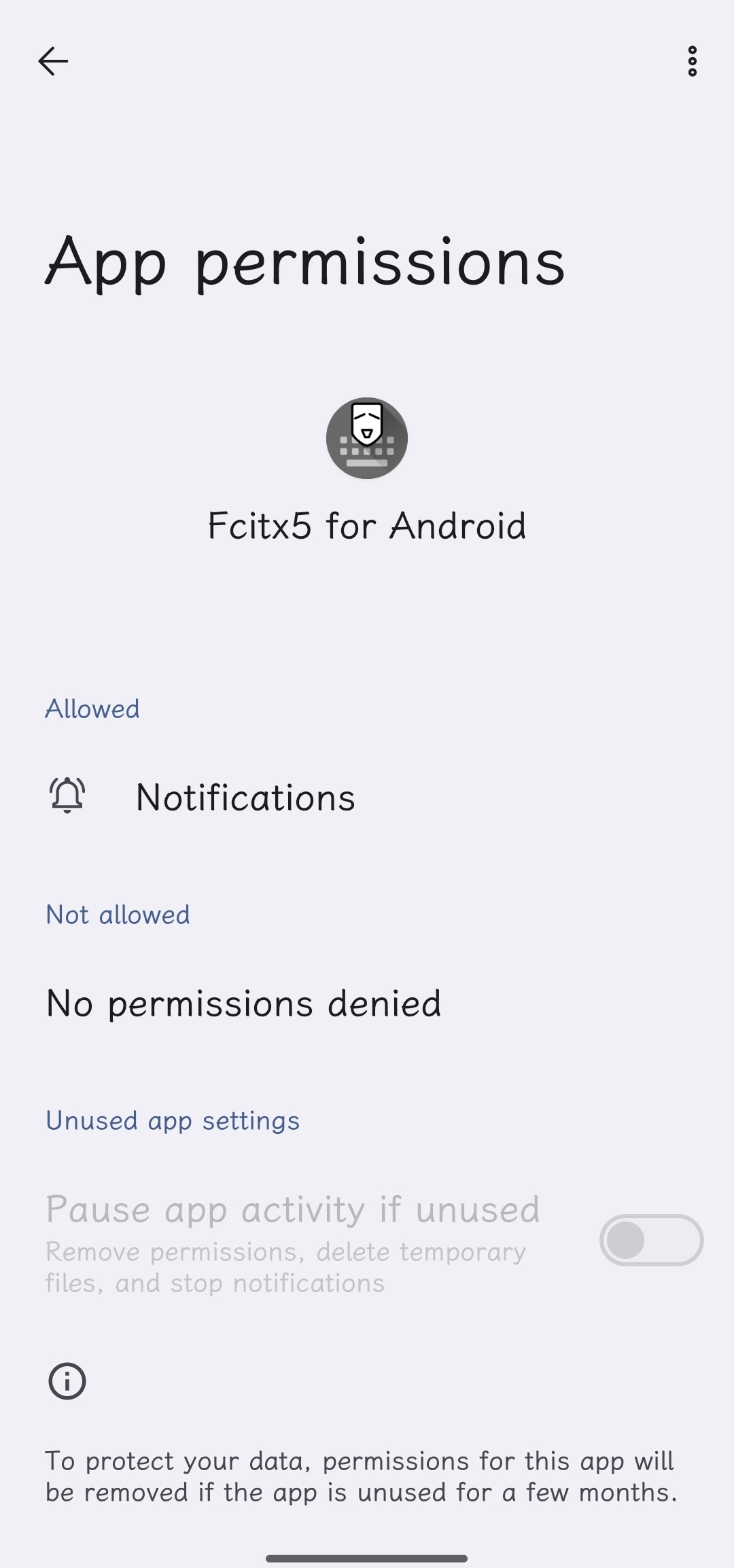
So use Fcitx 5 Android instead. It’s a open source IME application without requesting any permission except Notification, especially without network permission.
https://github.com/fcitx5-android/fcitx5-android
It’s stories like this that don’t surprise me as much as make me ask: How the fuck do you store and process this much data to get anything useful out of it.
You just save the first 50 digits typed after some email is typed, and you have all the passwords you need!
This only applies if a username is a email
And if it is then what happens when people actually email someone? Autocorrect during login?
I don’t think they’re saying that method would yield 100% clean data but it would give you all the “necessary” data with the absolute bare minimum storage requirement. At some point people will log into their email and for most people if you have their email password you have the password they use for everything
The people here acting like their Gboard doesn’t do the same is so funny.
Edit : never used nor installed tiktok.
It probably doesn’t though. Obviously it’s closed source making it harder to tell what’s actually happening, but there’s nothing stopping security analysts from looking at network usage and such. I would imagine that Google doesn’t install a keylogger on every Android phone, not out of the goodness of their hearts, but because they don’t want the bad publicity and lawsuits when it would inevitably be discovered.
they do collect usage stats by default though.
which include typed sentences passed through their ai model and words usage counts.
it can all be turned off and gboard seems to respect these options. it doesn’t access online services unless requested with these options off.
Imagine willingly installing a keylogger, lol
God bless gdpr